How to Take the Headache Out of Using Encryption

Sharing sensitive documents and information securely is business-critical, but a smooth user experience remains a core issue to encryption success.
How annoying would it be if every time you wanted to enter your home, you had seven locks to open? Probably irritating under most circumstances.
This concept is transcending to our digital world where security is increasingly differentiated by user experience, in addition to the protection services rendered. And, for enterprises looking to exchange sensitive information electronically, avoiding time-consuming and irksome experiences are imperative to doing encryption right.
Avoid Investment Failure by Improving Customer Experiences
Most organizations recognize the necessity of secure communication, with the numbers of enterprises without email encryption capabilities being few and far between. And yet, based on our research and surveys, over 90 per cent of IT leaders at these organizations describe their current processes of sending secure messages and documents as difficult – even frustrating.
“For me, this flags user experience as imperative when it comes to choosing an email encryption solution,” said Echoworx VP Customer Engineering, Chris Peel, in a recent interview with Help Net Security. “When it comes to sending a secure message or document, encryption is an important element in that you need to apply encryption as a usable feature. There are many factors which need to be considered to preserve a natural, and consistent, message flow anywhere on any device.”
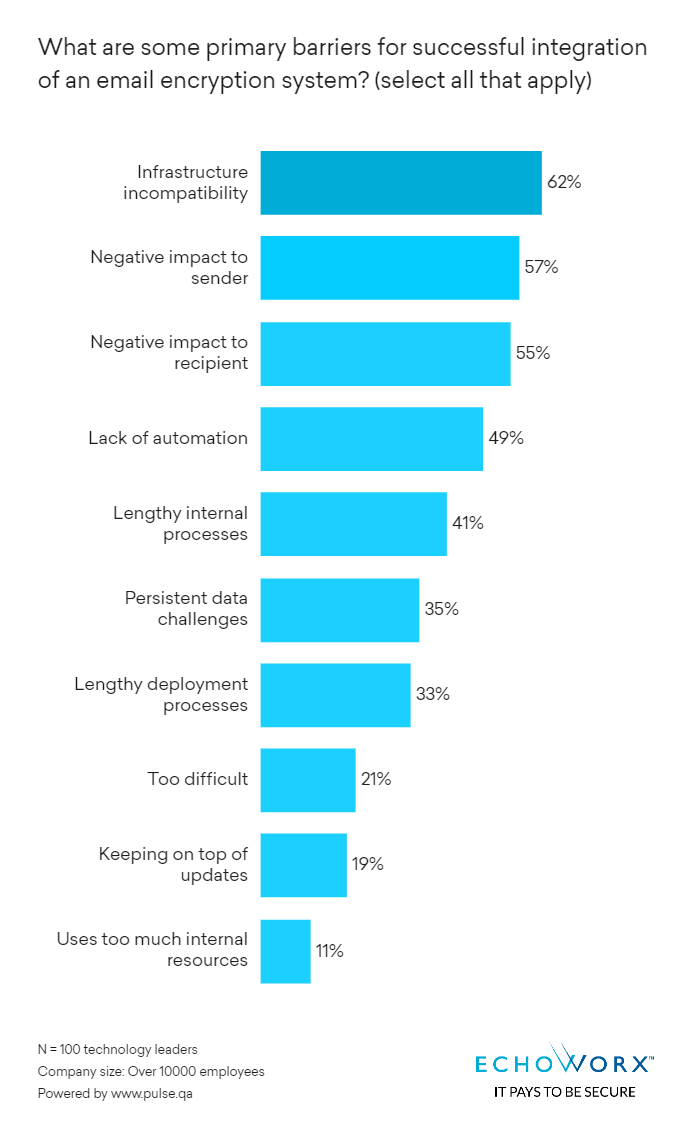
Enable Flexibility and Start Giving Users Choices
Adding simplicity to a secure communications process isn’t about simplifying security, it’s about finding the most-appropriate approach to sending and receiving protected documents and messages. While a more stringent authentication measure, like Multi-Factor Authentication (MFA), might be applicable for backend admin access, a more streamlined approach, like biometrics or social login, would be better for your customer-facing messages. You need to emphasize flexibility and offer personalized experiences at every step.
“Your enterprise might use TLS, for example, to send and receive sensitive messages and documents,” said Peel. “But what about instances where a TLS connection is not available? Or used, like we see in the EU where a reliance remains on PGP and S/MIME? You need to ensure seamless secure communication with all your business contacts, regardless of where they are located, how they choose to connect or what format the information they are sharing is in.”
Learn How to Buy the Right Encryption and Download Guide to Eliminate Old-School Criteria!
Stop the One-Size Fits All and Stay Ahead Jurisdictional Demands
From a pure technical point of view, compliance is viewed as a checkbox. Do you have encryption capabilities? Check. But international privacy jurisdictions, rules and regulations often go above and beyond simply being able to send a message or document encrypted – often governing how a secure message is sent, including the use of language elements in the branding, or how a secure message is protected both in transit and at-rest. Providing a personalized user experience which satisfies jurisdictional demands can be resource-intensive and time-consuming for your IT department to stay ahead of.
Peel said: “Imagine you’re a major British bank, for example, still adapting to Brexit’s effects on your business under the GDPR. You might acquire another bank, and let’s say it’s based in Manila. Do you know if your business is protected in Manila? Do you know how data must be stored in the Philippines? What do you know about local jurisdictional privacy rules governing data sent to, within and from the Philippines? Does this new business warrant forming a dedicated IT team to set up, deploy and run a secure communications system? (This is a challenge) we often see causing major headaches for enterprises struggling to implement effective ways to exchange sensitive information using encryption.”
That’s why Echoworx offers extensive branding controls along with our data centres in Canada, Ireland, the UK, Germany and the US, empowering you to decided where your data goes, is processed and how it is presented. Email encryption is all we do, it is our specialty.
If you would like to learn more about how Echoworx can help you prevent, address, overcome and eliminate email encryption roadblocks, please reach out to book a demo with one of our encryption experts.
What You Should Do Now
- Discover how email encryption can enhance your business in various scenarios. Book your PERSONALIZED demo today.
- To understand the power of advanced email encryption, check out our Resources. It offers valuable guides, updates on strategies, and case studies of successful clients.
