Eliminate Your Doubts About Using Social Connectors

You’d like to streamline access, reduce credential theft and improve your overall quality of service by offering third-party social connectors (OAuth) like Google or Microsoft to your customers.
Great!
You’re aligned with 64 per cent of IT leaders recently polled. But how do you convince the remaining? There tends to be a lot of confusion over what exactly OAuth access means, which social connectors you need and how to build consensus within your team.
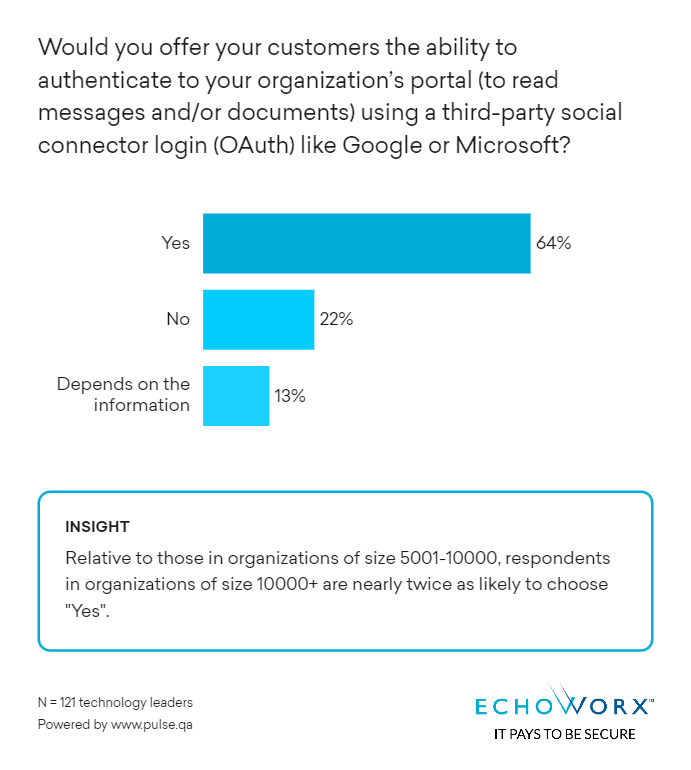
Here is how Echoworx positions OAuth for secure email:
Open Industry-Standard Protocol
OAuth is an open industry-standard protocol for authorization – meaning it is neither an API nor a service. OAuth utilizes unique and temporary access tokens, that represent authorization, on the user’s behalf. This means that any third-party web service can leverage it to grant access to a secure resource, without ever sharing any passwords and other sensitive information. And, only the individual user can authorize or revoke use of the third-party web service. So, theoretically, the more social connectors a product or service offers, the more customized your authentication experience can be for all your different users.
Configurable to Your Scenarios
When using third-party social connectors, a flexible approach can be the most effective—one that allows the ability to choose based on your scenarios and your diverse users. To this end, the OAuth capabilities of the Echoworx platform offers a growing list of social connectors, including Office 365, Google, Salesforce, Facebook, LinkedIn, among others to authorize access to a secure email resource. The process is transparent with the user in full control of granting or revoking access to the web services. Echoworx access to user data is only for the purpose of validating the email address.
One of our banking clients expressed concerns about offering additional social connectors aside from Google and Office 365. While another client wanted to offer access via social connectors by default. Our platform offers a full suite of social connectors with the ability to easily enable and disable specific social connectors, at the click of a button, from our web-based admin portal.
Simplifies User Experience
Pandemic-fueled burnout is leading to apathy and a lower guard toward workplace security, according to 1Password’s State of Access Report 2021. The research found that 84% of security professionals and 80% of other workers are feeling burnout, which has led to an “aren’t worth the hassle” security attitude. By allowing users to leverage social connectors, via OAuth, to access their encrypted email and documents, you can effectively make authenticating secure email a path of least resistance – reducing credential theft, while improving user experience, customer satisfaction and engagement.

Sourced from 1Password State of Access Report 2021
Streamlines Processes
When using encryption, organizations must always consider the potential impact on its recipients – new users in particular. A Single Sign-On (SSO) solution, like OAuth, can streamline the registration process. If activated, new users of our platform can skip the account registration process by simply logging in using their existing social network credentials. The first time a user authenticates with a particular OAuth provider, they are prompted to grant permission to access their basic profile information. All subsequent logins may be granted via a social connector of their choice. No more password lists.
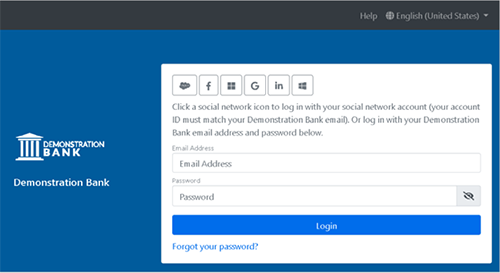
Subsequent logins may be done via an enabled social connector.
Easy to Deploy and Manage
Allocating additional resources to implement and support third-party social connectors can be a pain point for many IT teams – many of whom are already overworked, stretched thin and experiencing burnout. But by leveraging our as-a-service nature, you eliminate the complexity of implementation, allowing for authentication via OAuth to be configured and offered quickly. Organizations simply enable and publish social connectors according to their unique business requirements and customers needs.
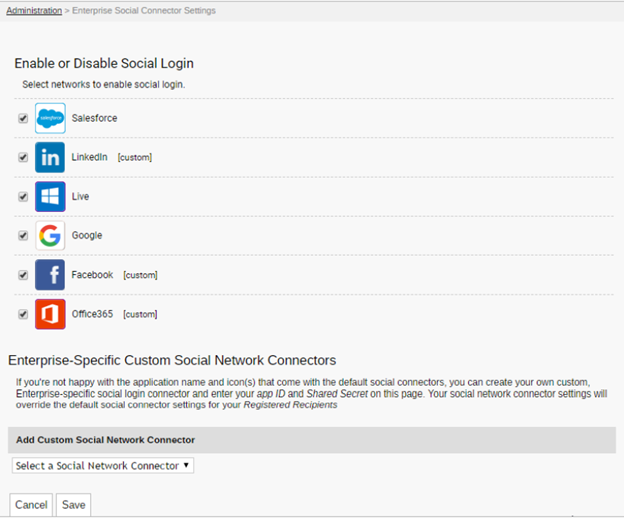
Adding and removing OAuth Social Connectors is possible at the click of a button
Bound by Strict Terms
Echoworx is bound by strict terms of use that protect the end user. These third-party Web API terms of use are publicly available.
- Google:
https://developers.google.com/terms/api-services-user-data-policy, https://developers.google.com/terms - Facebook:
https://developers.facebook.com/terms/dfc_platform_terms/ - LinkedIn:
https://legal.linkedin.com/api-terms-of-use - Microsoft:
https://docs.microsoft.com/en-us/legal/microsoft-identity-platform/terms-of-use
Our sole purpose is to protect the data and sensitive information you send. This is our specialty. To that end, Echoworx is committed to providing the highest level of security, controls and integrity to support our cloud security services. Our certifications and accreditations, demonstrate this commitment.
If you would like to learn more about the OAuth Social Connector capabilities of the platform or see a personalized demonstration, please reach out to book a demo with one of our encryption experts.
What You Should Do Now
- Discover how email encryption can enhance your business in various scenarios. Book your PERSONALIZED demo today.
- To understand the power of advanced email encryption, check out our Resources. It offers valuable guides, updates on strategies, and case studies of successful clients.
