This article is more than 1 year old
With ICMP magic, you can snoop on vulnerable HiSilicon, Qualcomm-powered Wi-Fi
WPA stands for will-provide-access, if you can successfully exploit a target's setup
A vulnerability identified in at least 55 Wi-Fi router models can be exploited by miscreants to spy on victims' data as it's sent over a wireless network.
Eggheads in China and the US have published details of a security shortcoming in the network processing units (NPUs) in Qualcomm and HiSilicon chips found at the heart of various wireless access points (APs). The flaw (CVE-2022-25667) prevents the devices from blocking forged Internet Control Message Protocol (ICMP) messages; these messages can be abused to hijack and observe a victim's wireless connectivity.
ICMP is a network layer protocol primarily used for diagnosing network traffic issues. It's mainly used for error reporting, though it can be misused for denial of service via ICMP flood attacks.
Evidently, the protocol can also be employed to evade Wi-Fi Protected Access (WPA) security in order to intercept and inspect a stranger's wireless network traffic. WPA – including WPA2 and WPA3 – is supposed to protect each device on a wireless network from snooping: the traffic between each client-router pair is individually encrypted so that other clients, even those on the same Wi-Fi network, can't sniff the radio waves and observe another's data as it goes over the air.
This particular attack is said to defeat that layer of security, allowing one device on a Wi-Fi network to intercept and snoop on the traffic of another device. The technique is described in a paper [PDF] titled, "Man-in-the-Middle Attacks without Rogue AP: When WPAs Meet ICMP Redirects," which is scheduled to be presented in May at the 44th IEEE Symposium on Security and Privacy.
The boffins who devised the attack – Xuewei Feng, Qi Li, Kun Sun, Yuxiang Yang, and Ke Xu, who are affiliated with Tsinghua University and Zhongguancun Lab in China and George Mason University in the United States – explain, "In this paper, we show that the designed functionality of wireless frames encryption at the link layer, which aims to prevent traffic hijacking in wireless channels, can be disturbed by the normal executions of ICMP errors handling at the IP layer, thus allowing an attacker to hijack the traffic of victim supplicants."
For this to work, the spy and their victim need to be on the same network – a public Wi-Fi network, for example. Also, the attacker needs to: be able to directly communicate with the victim's device via the Wi-Fi network; know the victim's IP address; and find an open UDP port on the victim's device – not impossible but not a given.
We also should say at this point that if the victim is not just relying on WPA, and safeguards their network traffic from eavesdropping by wrapping it in HTTPS, SSH, TLS, or some other form of encryption protocol, that extra encryption will still need to be defeated by the snoop before they can make any sense of intercepted Wi-Fi connections.
- How Wi-Fi spy drones snooped on financial firm
- Linksys forces password reset for Smart Wi-Fi accounts after router DNS hack pointed users at COVID-19 malware
- Wi-Fi kit spilling data with bad crypto – Huawei, eh? No, it's Cisco. US giant patches Krook spy-hole bug in network gear
- While Reg readers know the difference between a true hacker and cyber-crook, for everyone else, hacking means illegal activity
Essentially, the attack has multiple stages but the most interesting part of it involves sending to a victim's device an ICMP redirect message that's crafted to appear as though it came from the AP. The router should ideally discard this kind of bogus message when asked to relay it to a device on the network, as the router didn't actually generate the message, but instead the researchers found these spoofed messages are forwarded to devices anyway via the vulnerable AP. The receiving device is fooled into thinking the redirect message is legit as it appears to be from the access point.
The redirect messages cause the victim's device to ultimately reroute its traffic to another destination. A snoop on the network can send ICMP redirect messages, dressed up as though they are legit and coming from the Wi-Fi router, to a victim via the AP so that the victim's device eventually redirects its network traffic to a system under the spy's control, allowing the miscreant to siphon off and observe their Wi-Fi traffic.
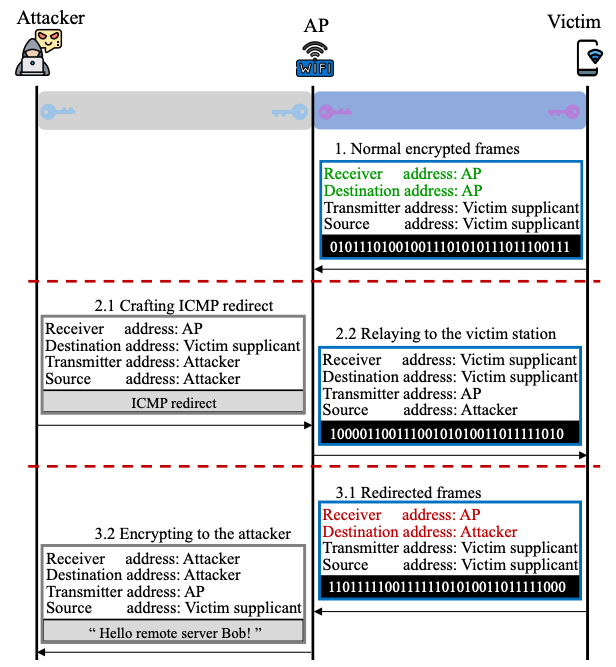
Diagram from the research paper ... This shows how an ICMP redirect message to an AP, relayed to a victim, can cause the victim to reroute and leak traffic data to the attacker
"[W]e discover that the crafted ICMP redirect message can always be successfully forwarded to the victim," the computer scientists wrote. "It cannot be blocked by the AP and existing security mechanisms.
"Due to the performance consideration, the NPU (eg, Qualcomm IPQ5018 and HiSilicon Gigahome Quad-core) in the AP router will directly forward the received fake message of ICMP redirects to the victim supplicant."
There are, as we said, other steps involved, such as discovering open UDP ports – needed to get the victim's device to accept the ICMP redirect messages, interestingly enough – and stripping away the WPA encryption. A video demonstration of the attack has been published here, along with diagrams that illustrate the necessary network interactions.
The researchers say they tested 55 AP products from ten vendors and none could block the forged ICMP messages. They also claim that 109 of 122 (89 percent) Wi-Fi networks tested were vulnerable to this attack.
Since this issue resides within the NPU, AP vendors need the help of the chipset makers to effect repairs. US-based Qualcomm was informed of the vulnerability in late 2021 and published an advisory last November.
Qualcomm did not immediately respond to a request to provide further details on the status of its patch rollout to customers.
China-based Huawei-owned HiSilicon, the researchers say, was also informed. And six of the 10 AP vendors cited in the paper have confirmed the flaw exists in their products. Some affected wireless APs, however, may still be unpatched.
Beyond NPU-based mitigation to filter and block spoofed ICMP redirect messages, the boffins proposed adding security checks to cross-layer network interactions. They say they prototyped a mechanism to do this in Linux 4.18 and have confirmed that it's effective. ®
