This article is more than 1 year old
Review: McAfee Endpoint Protection for SMB
Does it prevent oogly booglies from getting on my system? Yes? Good!
Anti-virus – sorry, endpoint security - programs suck. I loathe them and they have been the bane of my professional existence for the better part of 20 years. Despite the crushing, crushing sadness that they cause, the call came down to review Intel Security’s latest endpoint security product, McAfee Endpoint Protection Advanced for SMB and - against my better judgement - I don't completely hate it.
Given time, I might even grow to like it.
I am aware that, half of you reading this will burst a cerebral artery at the notion. How could you possibly say anything nice about them? Ladies and gentlemen, I hear and understand. I could try to write an article about the sleepless nights, endless support calls, broken updates, application incompatibilities and other bizarreness they have all thrown at me over the years.
Yet I fear that, if I tried, I would curl into a ball, hide in a corner and rock back and forth muttering something about Smurfs. To be clear upfront, in its cloud iteration, McAfee Endpoint Protection Advanced for SMB is a Windows-only protection suite. Mac users are catered for with the on-premises version, but for cloud Mac, Linux and mobile users need not apply. I'm not going to ding Intel Security for that; it is what it is, and this review will judge it in the context of other Windows protection suites.
So let's focus on what we want an endpoint security product to do. I have five criteria by which I judge endpoint security products:
1) Does it prevent oogly booglies from getting on my system? Yes? Good!
2) Does it prevent me from going to sites or running applications I want? Yes? Bad!
3) Does it get in my way and nag me all the time? Yes? Deorbit the tungsten impactors!
4) Does it have a UI that would make CA developers blush or Microsoft developers excited? Nope.gif!
5) Does it take care of third party app updates? Yes? Ply the developers with fine Scotch!
So, criteria established, let's wreck this thing.
Great Oogly Boogly!
In testing the prevention capabilities of I threw a standard barrage of tests at the thing and it survived. Note that this is a separate test from its ability to clean stuff that has managed to either sneak past the prevention defences, or that was already there.
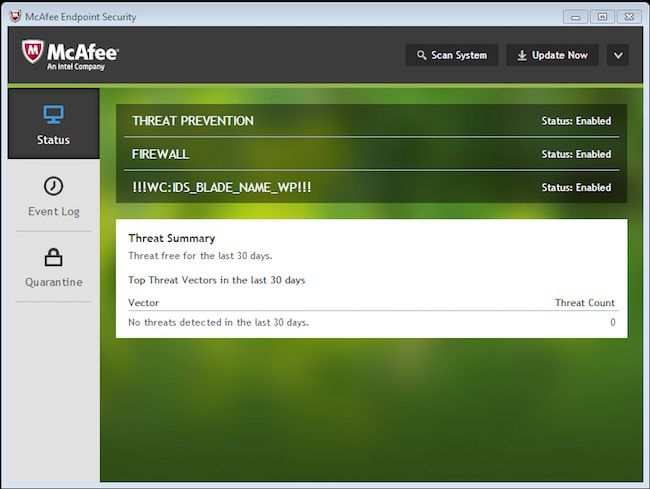
Intel Security’s Endpoint security comes with three primary sub-components. The first is an anti-malware scanner/threat protection widget that scans for general oogly booglyness. The second is a firewall. The third is a "web control" widget that takes the form of browser plug-ins to prevent you from doing anything overly stupid.
The first thing I note is that the latest version of Intel Security Platform Endpoint Protection (version 10) does not seem to support Windows XP 64-bit. That's unfortunate, because one of my biggest uses for proper endpoint security is to keep the old stuff that can't be updated humming along for as long as possible. It also doesn't support IE6, but I'm unable to feel sad about that.
Previous versions of Endpoint Security integrated into Outlook, so long as it was not the Office 365 variant. The current version doesn't seem to. Instead the documentation has a blurb about "monitoring the APIs" that I'm a little nervous about.
Exploit Prevention stops exploited buffer overflows from executing arbitrary code. This feature monitors user-mode API calls and recognizes when they are called as a result of a buffer overflow. Threat Prevention uses the Exploit Prevention content file to protect applications such as Internet Explorer, Microsoft Outlook, Outlook Express, Microsoft Word, and MSN Messenger.
If you dig around in the KBs enough you'll find that the reason the magic McAfee add-on isn't present in Outlook is because Outlook is unsupported in the current version. Thunderbird never got any love, and continues to be ignored.
I hope their API voodoo filter is good. To be fair, while I could play around with infected messages, I couldn't get them to trigger and do anything too horrible, and I couldn't save the attachments. On the other hand, it's been awhile since I put my hand to trying with any seriousness. I'm calling mail support undecided, with a soupcon of nagging "please don't fail".
Intel Security also sells a cloud-based e-mail scanning service that is separate from the Endpoint protection suite.
The Web Protection and Threat Protection portions of the equation certainly prevent the average malicious website, or trying to drop various virally infected files onto my system via Sync, USB stick, DVD, network, etc. Even when I started getting into the big guns and going for the code I keep on the drives with red tape Intel Security surprised me and kept the badness from gaining hold.
Now, browser protection is an interesting item. Chrome and IE were detected just fine. The browser plugins were injected. That said, the individual end user needs to activate the plugins before they start being protected. Considering that a huge part of the selling point is that this is an endpoint protection solution where you can push out policies across your entire company, this is a gotcha to be aware of.
Another gotcha is that it missed Firefox. The official documentation (from September) says it supports Firefox 30. I have Firefox 36. I am unsure if this is the reason my Firefox wasn't given a relevant add-on, but there we are. I cannot find a download on Intel Security’s site to get my own plugin.
I have a not unimpressive sample library of digital badness and all of it was prevented from doing its thing. I even took a dual Xeon 2680 v3 system with 256GB of RAM augmented by two Nvidia K2 GRID cards and threw a fuzzer a the firewall across a 56Gbit/sec Infiniband port for the better part of a day and came up with nothing.
Now, admittedly, a day isn't very long, but I've at least crashed other endpoint products' firewalls in half that time. To my astonishment, Intel Security’s firewall just soaked it up like a champ and asked for more.
I switched to heuristics testing and started coding some of my own stuff to see it if would pick up fresh strains. I tried coding to any number of known vulnerabilities and even a few that don't yet have CVEs* and it had no trouble. I'm assuming that this is because the vulnerabilities I got are fairly well known in the appropriate circles, despite not being on the list.
So am I satisfied with the general oogly boogly protection? I give this a qualified yes. Intel Security needs to step up its support of major applications and browsers. Outlook, Thunderbird and Firefox need love.
False positives
One of the biggest issues I have traditionally had with endpoint security products is that they block me from going to sites I need to or using applications that are critical. A good example of this would be Java applications for industry specific software. Endpoint security products love preventing them from talking to the network.
Sure enough, if I launch Supermicro's IPMIView (a Java application) Endpoint Security is having none of it. Network communication blocked. Do not pass go, do not remotely administer your datacentre. It seems to do this for all Java applications, and I gave up trying to find a way to create exceptions after an hour.
Insert a dramatic sigh here. It was going so well! I realise that when it comes to average everyday users, I probably don't want Java applications (note: not Java in the browser; that should be banned on general principle) communicating with the outside world. But I'd really like it if there was a convenient and obvious mechanism to tell the thing "no, bugger off, I need to use this!"
That said, It actually doesn't get in my way when visiting websites it should know perfectly well are acceptable. vSphere web client on the local subnet with a locally generated (and invalid, as far as the client browser is concerned) SSL certificate? Go right on by. It's not going to stop you.
Someone realised that vSphere is a thing that endpoint protection companies should care about, and they deserve a cookie.
Similarly, it let me manage my ioSafe without issue, log into the Tintri, work on Webmin websites and even go to a domain controller's /certsrv that wasn't part of my network. No grief, no fuss.
So this round is a draw. Endpoint Security still has an irrational hatred of Java applications, but seems to have twigged to the fact that lots of things are managed by browser, even with "bad" SSL certs.
Annoyance factor
Is the application annoying, naggy, covered in popups or otherwise constantly trying to remind you that it's there? This section is quick and easy: no. It's perfectly unobtrusive, and even the browser plugins are pretty sedate. Pass the bubbly 'round folks, you won this round hands down.
UI
I like the UI. Yes, that sound you hear is probably the rumbling of horsemen heralding an apocalypse, but I honestly like the UI.
The UI is simple, clean, and even relatively intuitive. There are no garish ubericons and no byzantine hieroglyphic tiles. The client application UI is pretty much perfect. I've pondered for a while and other than a "let me use my Java app you miserable git" button I can't come up with a single change I'd make. The SaaS management console UI is probably the single best such UI I've ever seen. They have a more usable start menu than Windows 10 by a country mile, and if your systems administrator is even half awake they'll figure out where all the bits are.
The hardest part of the whole exercise for me was figuring out how to set firewall policies. The secret is that the "policy catalog" is divided up by product.
It makes perfect sense to go looking in the policy catalog for policies to manipulate. It even makes sense to have to "duplicate" the default policy before you can make changes, and then assign that new policy to devices or groups. I just see no reason to break the policies up by product. Mostly because I'm bitter that I didn't see the pulldown for product and wasted 10 minutes trying to find the firewall rules.
Other than that, it's all really straight forward. Not straightforward enough for me to put an MBA in front of it and have them manage a small business' computer fleet, but anyone who actually understands what all the pieces of this software package are supposed to do will find the UI no trouble at all.
Intel Security isn't using any proprietary terminology. Everything is industry standard jargon, clearly labelled on a cleanly designed website in a logical and rational fashion. Clear win here for Intel Security, but I'm still trying to wrap my head around a McAfee UI – or, really, any modern UI – that doesn't have me inventing new expletives. It's kind of unnerving.
Third party apps
Sadly, the one place where Intel Security’s endpoint security falls down is updating third party applications. It simply doesn't do it. There isn't even a widget to tell you that a client system's java is out of date, let alone act on it.
Now, there's a quick solution to this. Intel Security could go hunt my man Sascha Kuzins over at Ninite down and give him a great big sack of cash. Integrating Ninite Pro's functionality into Endpoint Security would close the gap pretty effectively. Double bonus karma points if they kept the free site around, because, well, Ninite is amazing.
Judgement!
To recap: I gave Intel Security’s McAfee Endpoint Protection Advanced for SMB a qualified yes on keeping the oogly booglies out. Intel Security needs to step its support of applications and browsers like Outlook, Thunderbird and Firefox.
False positives are a wash: website false positives are kept to a minimum, but a "let me use my java application" button is required. Complete victory on not being annoying and on a great UI, but no love for third party app support.
There are enterprise-focused products that are more feature rich. To be perfectly blunt they're also a pain in the ASCII to use, right to the very last one. It's not perfect, but Intel Security’s endpoint security stands out amongst its peers as one of the very few I'd willingly use on my own systems.
I can run a midsized company off of this without having to dedicate an expert to the product. It's simple enough to manage thousands of endpoints but still be "just another application" that a generalist sysadmin has to use day to day. Will wonders never cease? ®
