This article is more than 1 year old
Google shores up G Suite against hapless users in the enterprise: App whitelist, physical security keys, and more
Notable omission from list of trusted stuff? Microsoft Outlook
Google has begun rolling out the beta of its Advanced Protection Program for enterprise, a set of stricter security policies intended for employees "most at risk".
A consumer version of the Advanced Protection Program is already available, and even the enterprise version is not completely new in that the security policies included can already be implemented separately, but it does bundle them together and makes it easier for admins to implement.
Google's suggestions for the most-at-risk users include admins, political campaigners, journalists, celebrities, business leaders, law firms, and anyone who deals with cryptocurrencies.
In reality, it may be better to regard almost everyone in an organisation as at risk since personal assistants or junior staff may otherwise be a route to accessing confidential information or impersonation.
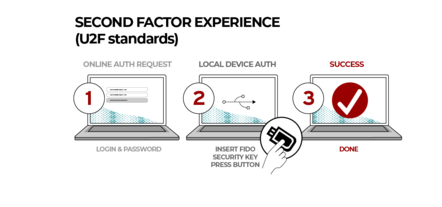
The set of policies starts with the requirement to use a physical security key, or rather keys. Users are required to have a main key and a backup key. Google's own Titan security key, which is now available in Europe for the first time, comes as a £50 bundle with a USB key and a Bluetooth key. You can also use keys from third parties such as Yubico.
The keys support FIDO U2F (Universal Second Factor), a standard from the FIDO Alliance and W3C which enables a strong second-factor device.
From the user's perspective, they have to register their FIDO device with Google, following which they will be prompted to press a button on the key when logging in. This protects against phishing sites since a stolen password is no longer sufficient. It is more secure than a code sent by SMS, partly because mobile phone numbers are vulnerable to account hijack, whereas a key device would have to be physically stolen, and partly because it is resistant to man-in-the-middle attacks thanks to verification that the service is communicating with the actual registered client.
Another policy is that only trusted apps are allowed access. The default trusted apps are Google-native apps, Apple-native iOS apps such as Mail, Calendar and Contacts, and Mozilla Thunderbird. Administrators can add to this list from a fixed list of available Android or iOS apps, or a web application with an OAuth2 Client ID – presuming it is the same as the current approach for whitelisting apps. You cannot use apps that need app passwords as this breaks the 2FA requirement.
Additional policies cover enhanced email scanning for viruses and phishing attempts, strict account recovery so this must go through an administrator, and download protection in Google Chrome.
Admins have to enrol selected users in the Advanced Protection Program, including the option of a date by which they must sign up. Once they do, users are signed out of all devices and apps and have to sign in again.
There is no additional cost to the Advanced Protection Program other than the physical security keys.
Google has also implemented anomaly detection in the G Suite alert center to notify admins of "potential data exfiltration risks based on unusual Google Drive behavior" – such risks being external file-sharing or downloads detected as unusual by Google's algorithms.
A side-effect of enabling Advanced Protection is that it makes it more difficult to use non-Google applications, though there is some support via the trusted application whitelist. It is not clear, for example, whether you can use Microsoft Outlook with Advanced Protection, though in Microsoft's latest version OAuth2 authentication works fine with Gmail. Of course it is easier to control security via first-party applications, but it can also be an obstacle to adoption. ®