This article is more than 1 year old
Pain spotting: Russia's Aeroflot Docker server lands internal source code, config files on public internet
Container images leak through insecure registry
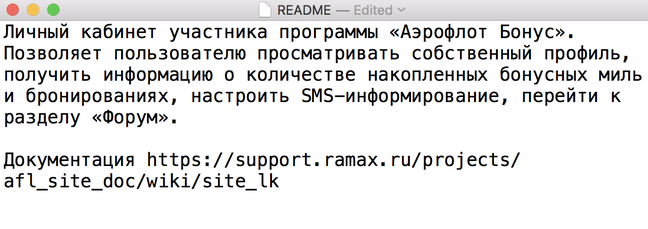
Exclusive Russian airline Aeroflot has exposed to the public internet the internal blueprints for its website, aeroflot.ru, The Register has learned.
Specifically, the biz has left a Docker registry server open to all the world to see: if asked nicely, with no authentication, it will cough up compressed archives of the confidential Python source code and settings text files that run its website. The files form Docker images that run on Aeroflot's website servers in containers. We have verified that the contents of the containers are present on the public website.
No sensitive customer information is believed to be among the leaked data. Aeroflot could not immediately be reached for comment on the matter: we have alerted the airline to the security blunder. We have decided not to link to the server exposing the information, nor go into detail on the data-leaking vulnerability, in the interests of responsible disclosure. Copies of the source code and configuration settings have been mirrored online, though.
The files cover all parts of Aeroflot's website – from handling gift certificates to issuing customer bonuses. They are a treasure trove for miscreants hoping to hack the dot-ru: any vulnerabilities found in the code or settings can be exploited to hijack the website, and snoop on passenger bookings and payments.
A source told El Reg on Wednesday they found a Docker registry server – used to deploy containers on servers – that had been erroneously left open to the public internet containing Aeroflot source code. We have verified that the leaky registry service is running on an Aeroflot computer. Normally, this would be hidden behind a firewall where access would be limited to Aeroflot servers and its developers.
Anyone who accesses the registry will be able to ask for the Docker images for the entire Aeroflot website. Basically, the blueprints for Aeroflot's website application. Again, while the repository contains the source code and config files for the web app, customer data itself is not believed to be present. Still, this is not a good look for Aeroflot, and could lead to bigger problems.
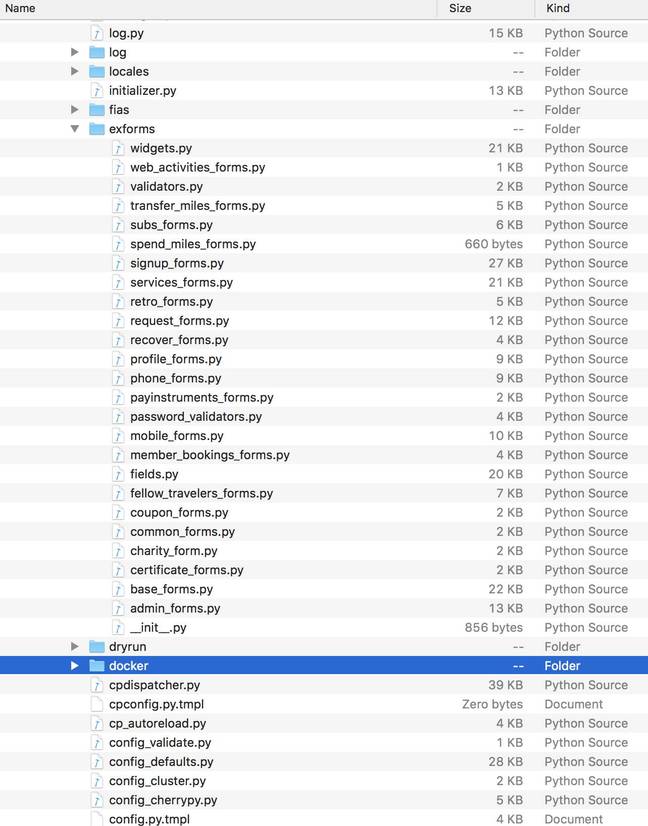
A partial list of internal Aeroflot source code found in the registry, and shown to The Register ... Click to enlarge
As you might imagine, this information would not be something the airline would likely want to have left open on the public internet, as this code would potentially allow someone seeking a way to breach the application to probe and prod at the source.
Think of it like someone being able to get the designs for your house. It's not the keys, but it would let them know where to look for an unlocked door or window. Were the applications securely written, this code would not be of much use, though the fact that the registry itself was left out in the open could suggest that there are other vulnerabilities.
Our source said they alerted us in an effort to get Aeroflot to improve the security of its IT operations, and to show that all companies, even large corporations, can make the common error of failing to properly secure their web-facing applications and tools.
Our industry insider also noted that the code is likely to have been exposed to the internet for years and, more likely than not, has previously been accessed by others and potentially exploited for attacks against the Russian airline.
"All the repositories are not protected in any way and there is no authentication," our source said. "Perhaps after this publication, the corporation will pay attention to its problems and will take care of ensuring information security."
The lesson for this is pretty simple: make sure all of the components of your developer environment and container setups are secure. In this case, an improperly configured registry with an open port has allowed a researcher to pull hundreds of megabytes worth of source code from a company. ®