This article is more than 1 year old
Encryption doesn't stop him or her or you... from working out what Thing 1 is up to
Why we hardly have to sniff the packet to know you play tennis with an IoT racket
You don't need to sniff clear-text Internet of Things traffic to comprehensively compromise a gadget-fan's home privacy: mere traffic profiles will do the job nicely, a group of researchers has found.
Encrypted streams can be surprisingly revealing, after all: just ask Cisco, which learned how to identify malware crossing the network boundary, without having to decrypt the data.
In this paper at pre-press site arXiv, nine researchers from Florida International University, Italy's University of Padua, and the Technical University of Darmstadt in Germany gathered data from household Internet of Things gadgets.
What they found is that even with encrypted payloads, light bulbs, power switches, door locks, speakers and the like reveal their activity in how, rather than what, they communicate: the duration of a traffic spike, the length of packets in a communication, packets' inter-arrival time, deviations in packet lengths, whether the user is contacting the device locally or over the Internet.
Once the researchers had sampled traffic from a selection of 22 devices (shown in the table below), the combination of unencrypted headers (MAC address and other information that helps identify manufacturers) with traffic patterns revealed not just what a device is doing (the light went on or off), but enough to infer what the user is doing (walking between rooms, sleeping, cooking and so on).
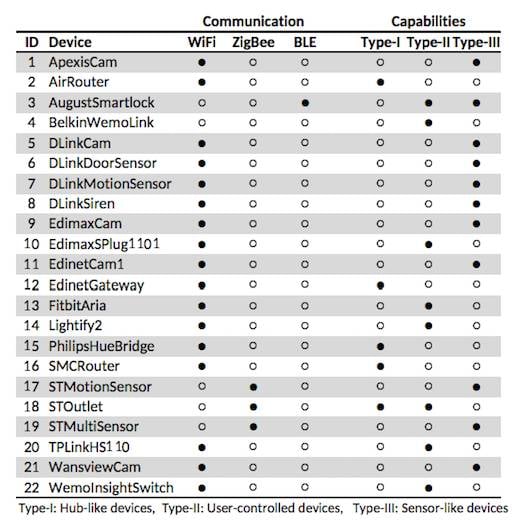
The more the merrier: devices tested in " Peek-a-Boo: I see your smart home activities, even encrypted!" (from arXiv)
“Our results show that an adversary passively sniffing the network traffic can achieve very high accuracy (above 90 per cent) in identifying the state and actions of targeted smart home devices and their users”, the paper said.
The four goals in the research were to: identify devices in a smart home setup; infer the user's daily routine from device traffic; infer the state of a specific device; and infer what the user is doing, based on the activity of multiple devices.
As a very simple example, the researchers wrote, a user walking through a smart home will activate lamps and motion sensors in a sequence that tells the researcher where they went, even without decrypting payloads.
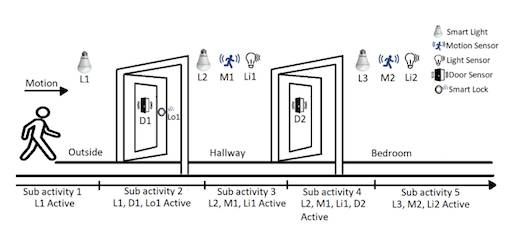
Walking through a home activates devices in sequence. Image: "Peek-a-Boo: I see your smart home activities, even encrypted!" at arXiv
That kind of information let the researchers craft what they called a “multi-stage privacy attack”: first, they gather traffic and classify it by protocol (for later analysis to find out what devices are using that protocol); second, the attacker tries to infer device state (for example, by identifying on or off transitions); third, they classify those states that can train the AI; and finally, they use a Hidden Markov Model to turn what they learn about the state of different devices into a way of inferring what the user is doing (sleeping, cooking, watching TV and so on).
If you don't want this kind of sniffing happening on your Internet, the researchers noted, you could use ToR or a VPN to encrypt everything (bar what an attacker can eavesdrop “over the air” if they can get close enough).
If IoT vendors want to protect their users (hint: they rarely do), it would be easy to pollute traffic streams with random false data so device state's harder to infer. ®
