This article is more than 1 year old
If you're serious about securing IoT gadgets, may as well start here
We're not here to fsck spiders – prove you care by getting busy with RADIUS and EAP
Can we overcome the SOHOpeless security of the Internet of Things at the home and small business level? An Internet-Draft from Ericsson engineer Mohit Sethi suggests so.
Sethi's ambitious proposal isn't destined for the hall of internet standards. Instead, it sets out a possible way to get IoT gadgets connected securely to the local network and internet, without trying to turn every home user into a seasoned sysadmin.
The goal is to help folks easily set up their gizmos without misconfiguring their gear, nor using weak or default passwords or no authentication at all. Rather than walk them through typing in Wi-Fi keys, it should all be mostly automated from the cloud. He noted that the supporting technologies for this already exist: RADIUS, EAP, and IEEE 802.1x aka port-based network access control. These are well-known but enterprise-focussed.
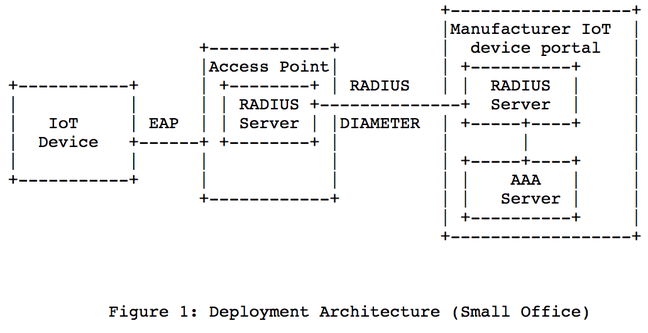
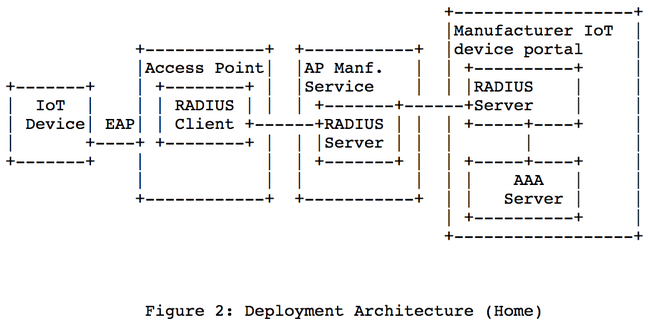
The draft describes how an IoT device can use EAP to securely join a Wi-Fi network and then securely connect to a RADIUS server to be authenticated and activated. This server could run on the wireless access point, or be an online service on the public internet run by the maker of the gadget. IEEE 802.1AR certificates present in the gizmo could be used for secure EAP-TLS authentication. This requires the wireless access point to support this system, of course.
Crucially, after you buy the device, you'd set a secret with the manufacturer that would be supplied when the thing is first turned on so that it can, via EAP and RADIUS, identify itself with the maker's backend – a classic Authentication, Authorization, and Accounting (AAA) system – and establish all the necessary credentials. At that point, the device can know when it's securely talking to its maker's backend systems, preventing man-in-the-middle attacks and the like.
Here's some snazzy ASCII diagrams of the setup from Sethi's proposal:
Sure, users might still have to play pick-a-passphrase when they buy a new device, but with the vendor's authentication infrastructure in place, the customer just needs it to register their toy.
“The online RADIUS server can prevent the user from registering the same (or similar) secrets for the different devices," Sethi explained in the draft. "This would ensure that devices in network do not share the same secret.”
While a good stab, some problems remain. For one thing, it requires an awful lot of effort on the part of gateway and device makers, who may resist splashing cash on setting up RADIUS and EAP services. In particular, the draft, written up this earlier month, doesn't address the thorny question of maintaining continuity of service and security if a vendor goes under, or decides to withdraw a product and its associated services. In other words, if the cloud service goes down, it'll likely take its gadgets with it.
Still, Vulture South feels it's a decent contribution to the debate and sits alongside similar approaches touted by Arm and Microsoft. We look forward to seeing what readers think in the comments. ®