This article is more than 1 year old
WPA2 security in trouble as KRACK Belgian boffins tease key reinstallation bug
Strap yourselves in readers, Wi-Fi may be cooked
Updated A promo for the upcoming Association for Computing Machinery security conference has set infosec types all a-Twitter over the apparent cryptographic death of the WPA2 authentication scheme widely used to secure Wi-Fi connections.
The authors of the paper have everything ready except the details of their disclosure: acceptance at the ACM Conference on Computer and Communications Security (CCS) for their paper Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2, a timeslot (during the afternoon of Wednesday, November 1), a so-far-empty GitHub repository, and a placeholder website at krackattacks.com.
So it seems Mathy Vanhoef of KU Leuven and Frank Piessens of imec-DistriNet are confident they really have done serious damage to WPA2 (the pair had previously verified vulnerabilities in WPA-TKIP, recovered cookies protected with RC4, and in 2015 improved their TKIP attacks).
According to Iron Group CTO Alex Hudson, disclosure is due some time on Monday, October 16 during European hours.
In the mean time, the name of the ACM paper is a hint at what's going on: Vanhoef and Piessens have attacked the handshake sequence WPA2 uses to choose encryption keys for a session between client and base station.
As Hudson notes, the attacker would have to be on the same base station as the victim, which restricts any attack's impact somewhat.
There's also a hint in this paper [PDF] Vanhoef and Piessens gave to Black Hat back in August. The slide below shows what part of the handshake the pair were working on.
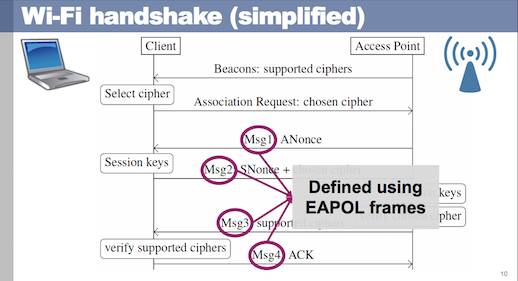
'Krackattacks' is the culmination of a long project attacking Wi-Fi protocols
So: get yourself some extra coffee this morning, dear readers, and wait for Krackattacks to drop. ®
Update: The CVE (Common Vulnerabilities and Exposures) numbers for Krack Attack have been reserved. They are CVE-2017-13077, CVE-2017-13078, CVE-2017-13079, CVE-2017-13080, CVE-2017-13081, CVE-2017-13082, CVE-2017-13084, CVE-2017-13086, CVE-2017-13087, and CVE-2017-13088. And there are now more details, here.
