This article is more than 1 year old
Flaws in web-connected, radiation-monitoring kit? What could go wrong?
Ripe target for ne'er-do-wells...
Black Hat Vulnerabilities in widely deployed Radiation Monitoring Devices (RDMs) present a potential mechanism for triggering false alarms and worse, according to research unveiled at Black Hat on Wednesday.
RDMs are used to monitor radiation in critical infrastructure such as nuclear power plants, seaports, borders, and hospitals. However, like many Internet of Things devices, security shortcomings provide a means to subvert their operation.
An inspection of the technology by Ruben Santamarta, principal security consultant for IOActive, uncovered flaws in RDMs from multiple vendors, including Ludlum and Mirion. Santamarta's research focused on testing software and hardware, firmware reverse engineering and radio frequency analysis.
The vulnerabilities create a means to meddle with "critical systems used for monitoring radiation levels, for example by falsifying measurement readings to simulate a radiation leak, tricking authorities to give incorrect evacuation directions, or increasing the time an attack against a nuclear facility or an attack involving a radioactive material remains undetected by sending normal readings to deceive operators".
Inspection of software that ships with the Model 53 Gamma Personnel Portal from Ludlum revealed a backdoor password. "As a result, malicious personnel can bypass the RPM's authentication and take control of the device, which could be used to disable it, thus preventing the RPM from triggering proper alarms," Santamarta warned.

Ludlum 53 and software [source: IOActive whitepaper]
Ludlum's gate monitors – Model 4525 – for vehicle inspection lack any security measure for data communication. Any attacker in the adjacent network can change the device's network settings, which opens the door to multiple attacks. Worse yet, the device communicates via cleartext, so attackers would be able to falsify readings, disable alarms, or perform any other originally supported operation.
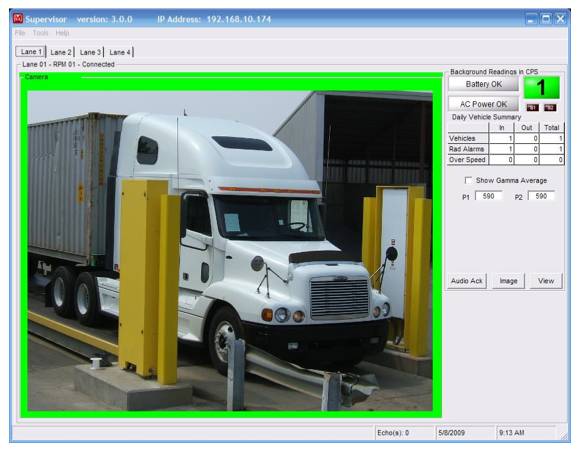
Ludlum's gate monitors – Model 4525 – for vehicle inspection [source: IOActive]
After studying the hardware and firmware, IOActive also uncovered potential attacks against Mirion WRM2-capable Radiation Monitoring Devices at nuclear power plants. A skilled and sufficiently motivated attacker might be able to forge or sniff "WRM2 transmissions, either by repurposing a Digi S3/S3B XBee Module or by implementing the XSC and WRM2 protocol layers in a SDR device". Such devices are located at secure facilities, reducing the likelihood of any attack in most scenarios. IOActive is convinced nonetheless that it has identified issues that merit remediation.
"Failed evacuations, concealed persistent attacks and stealth man-in-the-middle attacks are just a few of the risks I flagged in my research," said Santamarta. "Being able to properly and accurately detect radiation levels is imperative in preventing harm to those at or near nuclear plants and other critical facilities, as well as for ensuring radioactive materials are not smuggled across borders."

Exposed Digi S3B Module [source: IOActive]
IOActive informed the affected vendors of the findings weeks before Santamarta delivered his talk, Go Nuclear: Breaking Radiation Monitoring Devices, at Black Hat. Despite initial responses indicating the issues would not be addressed, more recent communications from some vendors have indicated work is being done to patch the critical vulnerabilities uncovered.
El Reg contacted Ludlum and Mirion for comment but we're yet to hear back from either.
A white paper on IOActive's research includes technical details for the testing conducted and the vulnerabilities identified. ®
