This article is more than 1 year old
Dev to El Reg: Making web pages pretty is harder than building crypto
'Brandis.io' secures messages with APIs and 445 lines of JavaScript, so good luck with crypto-cracking laws!
+Comment An Australian computer scientist working in Thailand has offered his contribution to Australia's cryptography debate by creating a public-key crypto demonstrator in less than a day, using public APIs and JavaScript.
Brandis.io not a useful encryption implementation (the site itself says as much), but is a useful public education exercise.
By using the WebCryptoAPI, author Dr Peter Kelly has implemented end-to-end crypto in just 445 lines of JavaScript code.
As Kelly writes at GitHub, “Brandis does not implement encryption itself; instead, it relies on the Web Cryptography API provided by your browser, and simply exposes a user interface to this API that enables its use by non-programmers.”
Hence its smallness: the cryptography is already out there, in the form of straightforward calls to public APIs: there's more JavaScript devoted to screen furniture than to generating public and private keys, or encrypting/decrypting the messages.
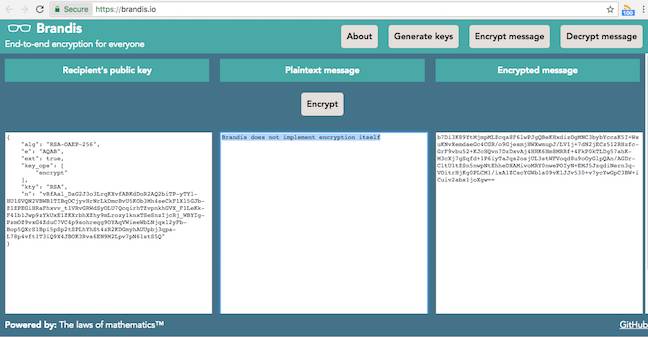
Dr Kelly's Brandis.io crypto demonstrator
As Kelly told Vulture South: “I spent way more time on [the presentation] than I did on the crypto-using code. Picking a colour scheme took longer than writing the code for generating a public/private key pair.”
Kelly warns visitors to the site not to treat this as a messaging platform: “Brandis is primarily intended as a demonstration; it was put together in less than a day. For real-world usage, we recommend more established software such as GnuPG.”
By the way, if you decide to try Brandis.io, note that its current message size limit is 190 characters. Kelly's investigating why that's so. ®
+Comment: Vulture South notes that kelly's efforts only addresses one part of the debate the Australian government ignited when its Attorney-General George Brandis fired the latest shot in what's being colloquially called “CryptoWars 2”. The other half is device security.
A common critique levelled at those who resist the idea of governments undermining encryption (the so-called “war on mathematics”, highlighted when Prime Minister Malcolm Turnbull unhelpfully quipped that Australia's laws will prevail over he laws of mathematics) is that they've got the wrong end of the stick, because messages could be recovered by means that don't attack encrypted messages in transit, but rather while they're at rest – for example, by recovering messages as stored on devices like iPhones or Androids.
First, it's worth keeping in mind that the government itself drew attention towards strong encryption, with its complaint that singled out specific end-to-end encrypted applications, and its promise to get platform-makers to co-operate (as well as device vendors).
More importantly, however, the argument that an endpoint compromise is okay ignores history. Whether it's the sloppy IoT security let the Mirai botnet hose big servers or the leaked NSA tools that let loose ransomware rampages, or the DNS Changer malware attack that began in 2006, there's ample evidence of the danger posed by insecure endpoints.
“You can't have security if you have insecure endpoints” was first expressed to this writer in the 1990s, and it's still true. We can't redirect concerns about weak cryptography by saying “you can still have strong crypto, if vendors will make weak devices”.
Even the NSA couldn't keep device exploits secret, after all. ®
