This article is more than 1 year old
OLE-y hell. Bug in MSFT Word allows total PC p0wnage
FireEye, McAfee, disclose over the weekend. Will Microsoft squash it on Patch Tuesday?
All eyes will be on Microsoft's April patch run - due tomorrow - to see whether Redmond gets ahead of a nasty Word zero-day that popped up last week.
The hack exploits Object Linking and Embedding and the FireEye researchers who discovered the bug were working with Microsoft, but were pre-empted by a disclosure from McAfee.
McAfee and FireEye each explain that the attack works all the way up to Office 2016 running on Windows 10.
A nasty aspect of the attack is that unlike many Word-based attacks, it doesn't ask the victim to enable macros.
A document e-mailed to a victim contains an embedded OLE2link object, and if the target opens the file, winword.exe contacts a remote server over HTTP, and a malicious .hta file disguised as RTF (rich text format).
Once the HTA application is loaded and executed, it terminates winword.exe to hide a dialogue raised by the OLE2link object. It then downloads additional payloads, and loads a decoy document for the user.
McAfee's post adds: "the attacker gains full code execution on the victim’s machine", and the bug "gives the attackers the power to bypass any memory-based mitigations developed by Microsoft."
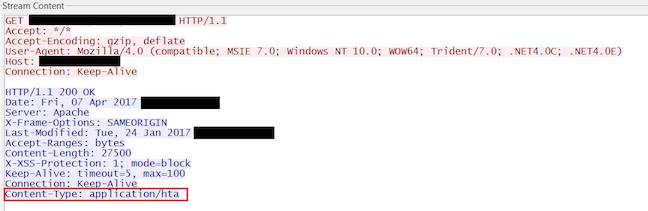
McAfee's screenshot of the bug
McAfee says the attack “cannot bypass the Office Protected View, so we suggest everyone ensure that Office Protected View is enabled”.
FireEye says it's taught its e-mail and network products to detect the attack. ®
