This article is more than 1 year old
Software exploits overrated - it's the humans you need to be watching
Dumb passwords and phishing the main threats
Video Weak passwords and phishing offer far easier mechanisms for breaking into most organizations than exploiting software vulnerabilities.
A study by US cybersecurity firm Praetorian based on 100 penetration tests and 450 real-world attacks discovered that stolen credentials offer the best way into enterprise networks.
Software vulnerabilities fail to make it into Praetorian's top five:
- Weak domain user passwords (a root cause of compromise in 66 per cent of cases).
- Broadcast name resolution poisoning (aka WPAD – 64 per cent).
- Local administrator attacks (aka Pass the Hash – 61 per cent).
- Cleartext passwords stored in memory (aka Mimikatz – 59 per cent).
- Insufficient network access controls (52 per cent).
Ninety-seven per cent of organizations have more than one root cause of compromise. The practical upshot of the report is that there should be more focus on guarding against stolen credentials and network segmentation as defenses, rather than playing "whack-a-mole" with software vulnerabilities.
Hackers most commonly use stolen credentials, often first obtained through phishing or other social engineering, to break into targeted networks and (eventually) gain access to sensitive resources, sometimes as part of a multi-stage process.
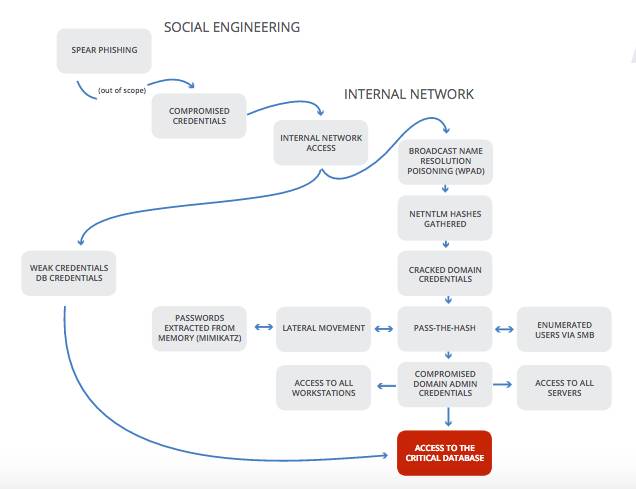
Sample attack anatomy [source: Praetorian white paper]
Although the methodology of the study was more focused on the playbook pen testers than adversarial hackers (hacktivists, financially motivated cybercrooks and intel agencies), the study still offers insights. For example, it goes some way towards explaining why hackers focus on spear phishing and other social engineering-style attacks rather than scanning for and exploiting software vulnerabilities – which Praetorian characterizes as "noisy" and in any case unnecessary to the process of identifying site-wide vulnerabilities.
"Social engineering will always be successful to achieve initial access to an organization," Joshua Abraham, practice manager at Praetorian told El Reg. "One percent of employees will always be susceptible to social engineering attacks."
"Organizations should put controls and processes in place to reduce the blast radius when an attack is successful. Therefore our research was focused on the attack vectors that are used after the initial access has been achieved. This can be used to focus defensive efforts based on the attacker's playbook," he explained.
Abraham added that Praetorian's findings were consistent with the methodology of nation state attacks as outlined by Rob Joyce, NSA Tailored Access Operations chief, at the recent USENIX Enigma conference. Notes from this presentation can be found here.
Black hats also make more reliance on stolen credentials than is commonly imagined, according to Abraham. "Looking at how HackingTeam was breached, the tools are consistent with our approach as well. The main difference is that black hat hackers are not limited by scope, rules of engagement and the timeframe of the engagements," he said.
Access to Praetorian's full (16-page) report can be found here (email address registration required). ®
