This article is more than 1 year old
Reminder: IE, Edge, Outlook etc still cough up your Windows, VPN credentials to strangers
Take precautions – like using a strong passphrase
Updated Microsoft software still leaks usernames and password information to strangers' servers – thanks to an old design flaw in Windows that was never properly addressed.
These details can be used to potentially unmask VPN users and commandeer Windows accounts. They can be obtained simply by tricking victims into visiting malicious websites or opening dodgy emails. It still works even on the latest builds of Windows 10 – Microsoft is unlikely to fix this any time soon.
The infosec world has known about this shortcoming for years; if it's news to you, read on.
Whenever Redmond's software encounters a link to an SMB network share, it attempts to log into it using the user's credentials. Imagine accidentally clicking on an smb://cool.domain.bro/receipe.pdf link in an Outlook message, or using Internet Explorer or Edge to visit a webpage with a hidden image that has an smb:// URL: Microsoft's software will follow the address, reach the SMB file server, and try to log into it using your credentials to fetch whatever file is needed.
In doing so, it automatically hands over your computer's login name and an NTLM hashed password, which can be cracked in seconds if you have a weak passphrase. This could be bad news if the file server is malicious and simply wants your details to compromise your gear.
You can check out the kinds of information leaked by your computer – including any login details – by visiting this test site with Internet Explorer or Edge (obviously, use at your own risk).
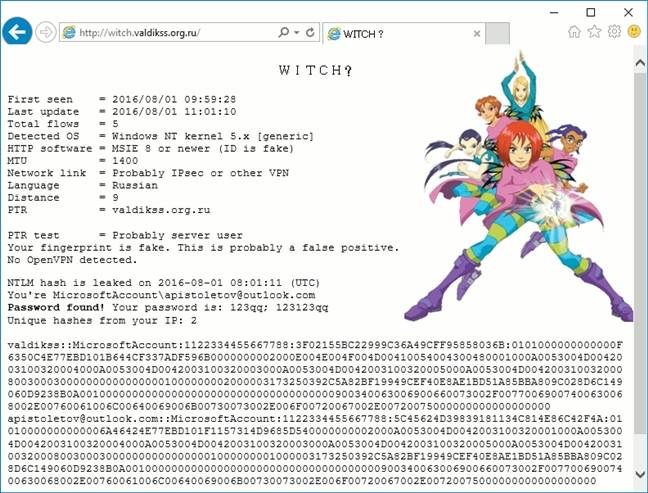
Oops ... What the above test site looks like if you leak an NTLM hashed password
This design flaw was highlighted in March 1997 and again at Black Hat last year [PDF]. It wasn't considered a big deal for most people because it wasn't possible to log into their PCs over the internet even if you knew their local username and had cracked their password hash. It was mostly a problem for IT departments: you could, from their connecting IP address, deduce where a victim worked, and if they had a weak password, crack it and try using it to log into other corporate services – such as their email or VPN. People love reusing passwords.
Then Windows 8 encouraged people to use their Microsoft cloud accounts to sign into their PCs, and Windows 10 made it the default. That means when Outlook, IE and Edge fetch an smb:// URL, they hand over your Microsoft account username and hashed password. That username is usually your email address, so if you're hiding behind a VPN or some other anonymizing service, you'll give away your registered contact info.
If you're able to crack someone's Microsoft account login, you can potentially drill into their OneDrive cloud storage, Office account, Xbox Live account, Bing search history, any associated Windows Mobile device, Outlook inbox, and Skype account.
It gets worse: if you use Windows' built-in VPN software – such as IPsec or PPTP – with MSCHAPv2 authentication, your PC will send not your local login details but your VPN service username and hashed password to potentially malicious SMB servers.
"The old security issue which was considered harmful only for business now can be easily used on home users," said security researcher Valdik, who goes into lots more detail about the design blunder here. He blogged about it in Russian, too. Valdik, who published his research on Monday, said he successfully exploited the flaw on three Windows 10 machines.
Here's a video of him receiving hashes after using Internet Explorer and Yandex webmail to open a message that contains a file:// URL to an SMB share on the internet. IE fetches the file, handing over his login information in the process.
VPN provider Perfect Privacy says it has blocked SMB port 445 on its network and updated its software to stop the handover of VPN credentials. It also warns against using Microsoft's software over the 'net and to not use a Microsoft cloud account to log into your machine. You should also, as always, use strong passwords that cannot be easily cracked.
The biz explained:
This was not considered a big problem when the attack only leaked local Windows login information (as in most cases you cannot connect remotely with those credentials). But since Windows 8, Microsoft allows to login to your computer with your Microsoft Live account and since Windows 10 this is the default. As result, this compromises every single service you signed up with your Microsoft account, including email, Skype and- XBox Live.
While this is not a VPN related issue, it also affects VPN connections: when using an IPSec VPN connection, a successful attack will not reveal your Windows credentials but the username and password of your VPN connection. While this does not affect the security of the encryption of the VPN tunnel, it may compromise the anonymity of the VPN user. Also VPN login credentials of company VPNs (e.g. for external service agents) may fall into the hands of an attacker.
Even if VPN would not be affected, we still feel it is our responsibility to protect our users from such blatantly open security holes.
Microsoft had no comment at time of publication. This design cockup affects Redmond's software. Chrome and Firefox do not normally cough up your credentials, although if you cut'n'paste a malicious file:// URL into Chrome's address bar, it can be fooled into fetching from an SMB share. Essentially, any application that calls URLDownloadToFile() to an SMB server, friendly or not, will hand over your information. ®
Updated to add
"We’re aware of this information gathering technique, which was previously described in a paper in 2015. Microsoft released guidance to help protect customers and if needed, we’ll take additional steps," a Microsoft spokesperson told El Reg.
