This article is more than 1 year old
Reinvented ransomware shifts from pwning PC to wrecking websites
'CTB Locker' targets WordPress, offers live chat to help victims pay up
A new ransomware variant appears to be ripping through WordPress sites encrypting data and demanding a payment of half a bitcoin to release files.
The website variant of CTB Locker is encrypting all files on WordPress-powered sites and replacing the index.php with a file that displays instructions for paying the ransom.
It even sports a chat room support feature where verified victims can exchange words with ransomware scum.
Researchers Benkow Wokned (@benkow_) and Tomas Meskauskas (@pcrisk) found the malware, warning it has likely infected hundreds of sites.
Victims can decrypt two separately-encrypted files for free in a bid by attackers to demonstrate the legitimacy of the ransom demand.
A means to decrypt files encrypted by the attack does not yet exist, meaning victims must pay if they want their files restored and do not have a backup.
Bleeping Computer blogger Lawrence Abrams suggests the new and burgeoning ransomware is targeting WordPress sites. Here's his thoughts on the matter:
Once the developer (attacker) has access to a site, they rename the existing index.php or index.html to original_index.php or original_index.html. They then upload a new index.php that was created by the developer that performs the encryption, decryption, and displays the ransom note for the hacked site. It should be noted that if the website does not utilize PHP, CTB-Locker for Websites will not be able to function.
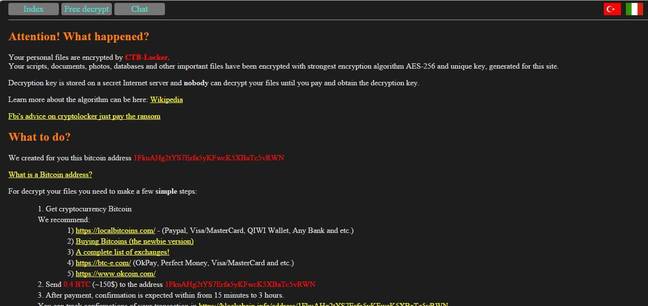
A CTB Locker message left on a currently infected site.
A random scattering of sites and businesses have been affected. One Milton Keynes, UK company which manufactures machinery for the healthcare and tobacco industries has been hit. Wokned has uploaded the ransomware source code to Kernelmode for other researchers to study.
Ransomware is regular flayed by white hat malware researchers who hunt for cryptographic implementation flaws that allow decryption to occur without need of the key.
Those attacks are typically baked into point-and-click tools and dsitributed to users for free.
BitDefender destroyed one hopeless ransomware team's encryption dreams after it found and exploited design flaws in three variations of the Linux.Encoder ransomware.
That led a sarcastic security industry to proffer cryptography tips to the tragically determined black hats. ®
