This article is more than 1 year old
3ROS exploit wins plaudits for the prettiest Mal-GUI ever
Options make pwning as easy as ordering pizza
The 3ROS exploit kit is one of the most user-friendly malware tools to have emerged and will likely spawn variants, malware men say.
Exploit kits are the preferred method of infecting large numbers of web users. The malware often packs a series of known and zero day exploits against major browsers and software like FireFox and Java which help foist payloads onto machines.
It is not the most advanced or popular exploit kit but authors Aditya K. Sood from Elastica and Rohit Bansal of SecNiche Security Labs say it is slick and should serve as a model for other crims.
They say in the Virus Bulletin paper 3ROS exploit framework kit – one more for the infection road [pdf] they have tracked the exploit kit for five months and it has possibility morphed into another capable kit dubbed Hunter.
The 3ROS authors used various techniques to make the infection process "smoother" during drive-by download attacks making it appealing to criminals.
"From a management perspective, the design of 3ROS is very advanced and one can expect that the same source code will be used in different ways to generate more variants," the duo says.
"We believe, based on indicators including the language and terminology encountered during the analysis of the 3ROS exploit kit, that it is of Russian or Ukrainian origin."
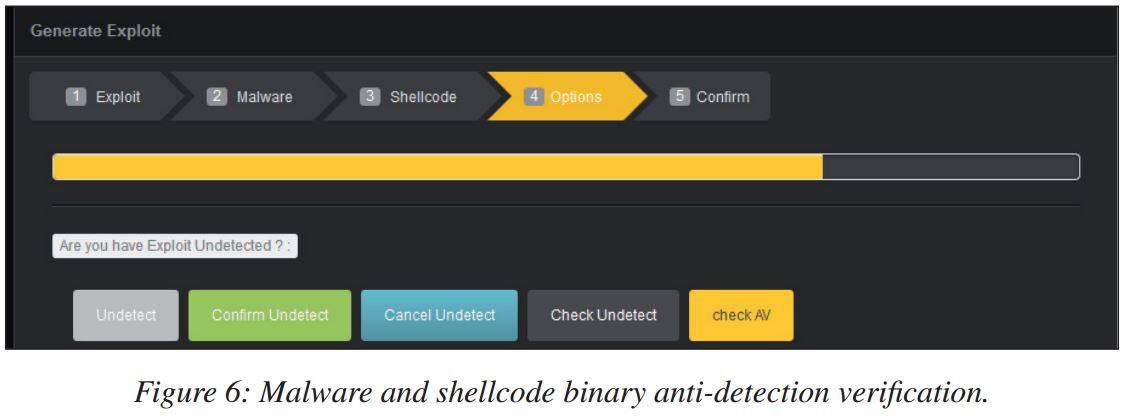
The pair says crims can use the slick GUI to choose their preferred exploit, malware, and shellcode, before offering to upload the unholy creation to anti-virus-checking services.
Malware and network-compromising web scum will be happy with choices offering better shellcodes that will add an account onto infected machines or 'download and execute' code that will run a payload. Here's what the researchers have to say about the exploit kit:
For cases in which the attacker is more interested in gaining control of the compromised machine than in delivering malware, the exploit kit supports shellcodes for the direct binding of a shell on the provided port, executing a reverse shell, and adding an unauthorized account to the compromised machine. The attacker can easily configure the shellcode arguments for all the shellcodes by supplying information as required by specific network environments.
Web scum will also receive updates through a notification system which alerts for new exploits and services. ®