This article is more than 1 year old
Terracotta: The Chinese VPN that hides Beijing's hackers with pwned biz
RSA report fingers globe-spanning, server-slamming hack network
BlackHat A China-based virtual private network (VPN) provider is powering some of the world's most capable hacking crews by selling infrastructure access stolen from at least 30 hacked businesses, RSA says.
The company, which RSA codenamed 'Terracotta VPN', claims to have 1500 mostly-Windows nodes from 300 organisations distributed across China, the US, and South Korea.
Of those, 1095 are found in China, 572 in the US, two in Britain, and one in Australia.
Lead RSA researcher Kent Backman, together with Alex Cox, Steven Sipes, Ahmed Sonbol, and others from the incident response and labs teams published the findings in the paper Terracotta VPN: Enabler of Advanced Threat Anonymity [PDF] to be presented at the BlackHat conference in Las Vegas this week.
Advanced attack groups including Deep Panda have used the illicit infrastructure. Hacked organisations powering the network include an unnamed Fortune 500 hotel chain, US Federal Government contractors, a US county Government, universities in Taiwan and Singapore, and scores of small businesses.
"This report by RSA Research may represent the first exposure of a PRC-based VPN operation that maliciously, efficiently and rapidly enlists vulnerable servers around the world," the researchers wrote.
"It is the first time RSA Research has seen DeepPanda and other similar APT (advanced persistent threat) actors using such networks for anonymisation and obfuscation."
The team posits that Terracotta would save significant cash hosing servers on the internet rather than juggling some 300 international transactions a month.
"RSA Research proposes that the Terracotta VPN provider hacks and harvests VPN nodes because this process is not only cheaper, but logistically easier than running a complex accounts payable operation required to maintain a global 1500-plus node VPN ecosystem."
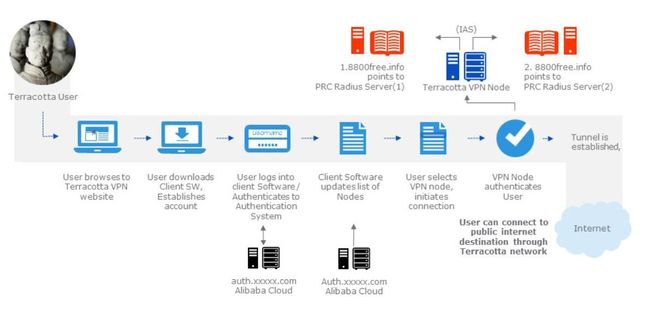
The VPN flow.
Moreover, hacking businesses offers APT scum the cover of a non-blacklisted exit node through which to target organisations: A hacking team stands a better chance at maintaining covert reconnaissance of a target when the packets trace back to a benign company.
To date, suspected Beijing-backed hacker groups have used at least 52 nodes to exploit Western governments and organisations. DeepPanda, also known as Shell_Crew, used 11 Terracotta nodes of a total of 13 when it popped an unnamed sensitive organisation. Terracotta uses that same tactic to hack organisations to increase its node count, RSA says, adding that most hacking took place on weekends, and out of work hours.
"The attractiveness of the Terracotta ecosystem to advanced threat actors may be strictly utilitarian: a very low-cost platform for attacks that serves to ultimately reduce the probability of detection."
The villainous organisation operates through a series of vanilla websites linked to common domain registration and often hosted on the same IP infrastructure.
Its claimed 1500 nodes is an inflated figure on account of some being "massive multi-homing" devices.
Researchers say the hacked businesses used other internet services but did not employ remote access or VPN, which helped attackers avoid detection.
None of the hacked businesses used hardware firewalls to protect internet-facing servers.
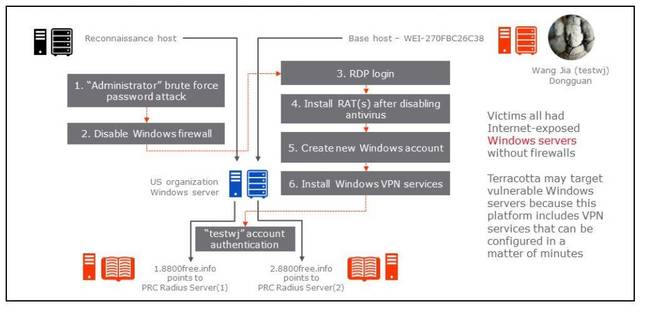
How one hack took place.
Terracotta hacking steps
| 1. Brute force password attack on the Administrator user account, via DCOM Windows Management Interface (WMI) through TCP port 135. There are multiple security testing tools with this capability, including the popular CoreImpact python class wmiexe.py1. The brute force activity was done from an IP address we call the reconnaissance host which was recently observed performing port 135 scanning on the internet, according to DShield2.
2 Remote connection using Administrator credentials from the reconnaissance host several hours later to disable the Windows Firewall and install the Telnet Service. Windows logs for this event sequence are consistent with those that would be recorded with use of standard remote administration tools available from Microsoft Management Console (MMC) via standard Windows Management Interface (WMI) protocols. 3 Login in via Remote Desktop (RDP) from a Windows system we call base host, with hostname WEI-270FBC26C38, originating from IP ranges in the vicinity of Dongguan, a suburb of Guangzhou, China. This happens within minutes of events in sequence number two. RSA Research has obtained forensic images indicating that this hostname was used for compromises and enlistment from January 2014 to June 2015. 4. From base host, uninstall Windows Defender and download and install custom Gh0st Remote Administration Tool (RAT) (dropper MD5: bccbba3ed45ead051f56fc62fef005a6) and/or custom Mitozhan RAT (MD5: 7b18614df95e71032909beb25a7b1e87) and a Windows backdoor shell daemon listening on port 3422 (MD5: 531d30c8ee27d62e6fbe855299d0e7de). 5. Creation of new Windows account (actual examples include “mssql” and “krto”) and addition of account to administrators group, from base host. 6. Days later, a login via RDP from base host in Dongguan, China using the account created in step five to install Network Policy and Access Services and Routing and Remote Access Services with custom remote access policy pointing at Terracotta Internet Authentication Services (IAS) servers. 7. Testing of Terracotta VPN centralised IAS authentication using “testwj” account from base host WEI-270FBC26C38. |
®
