This article is more than 1 year old
Nigerian prince swaps the sweet talk for keyloggers and exploits
Their emails still reek, but non-English natives don't notice
Nigerian 419 scammers have taken to the crime-as-a-service model using cash to plug their technical capability shortfalls to build malware campaigns that could be making millions, according to FireEye researchers.
Erye Hernandez, Daniel Regalado and Nart Villeneuv said that scammers, notorious for their attempts to fleece the gullible, were now targeting users with exploit tools and keyloggers and breaking into legitimate business email transactions to swindle buyers and sellers.
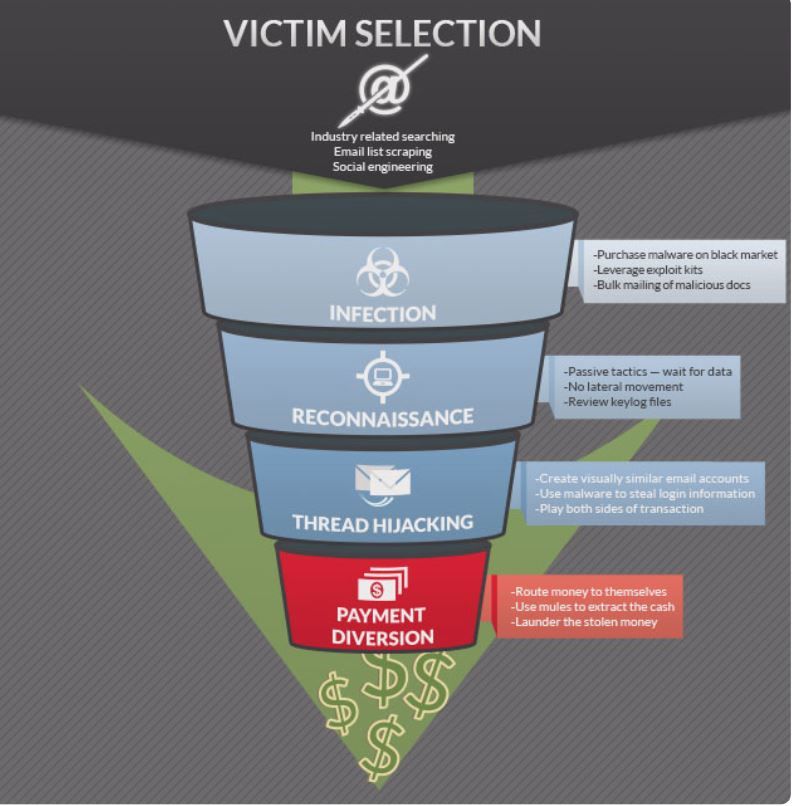
The team said, in a report entitled An Inside Look into the World of Nigerian Scammers (PDF), that this was the first time the end-to-end activities of the group had been detailed.
"FireEye Labs discovered an active operation of a group of cybercriminals involved in multiple executions of the payment diversion scam," the team added.
"The group is composed of loosely organised individuals who use basic, but effective, tools to defraud their victims of thousands of dollars.
"We estimate the group has targeted 2,328 victims in 54 countries [preferring] small to medium businesses in Asia because they are non-native English speakers and are usually not as technically savvy as big businesses."
The criminals will pay up to US$3,600 for malware tools including encryptors, builders, remote access trojans, and various info-stealers, using the tools to con users out of cash ranging from thousands to possibly millions of dollars.
The report illustrated one of the ways in which luddite scammers can use efficient cybercrime services to break into the malware game, and the effectiveness of targeting non english-speaking countries in a bid to conceal otherwise noticeable grammatical errors.
FireEye examined one Nigerian collective of at least four individuals who shared a single command and control server. They used the popular Microsoft Word Intruder tool, and keyloggers HawkEye and KeyBase, buying the MWISTAT builder to track the effectiveness of their campaigns.
They shared tools and traded tips, with more experienced scammers offering potential victim lists to noobs.
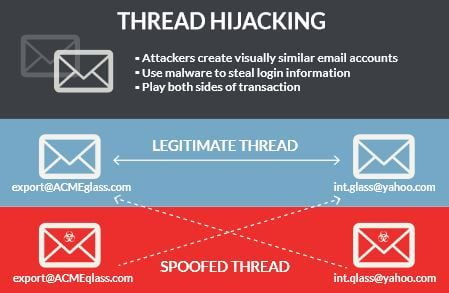
While tactics vary, the scammers will generally gain access on an email account and identify threads regarding business transactions. They then create spoof threads contacting buyers and sellers in a bid to obtain financial data.
The researchers said scammers will peruse sites like Alibaba in a bid to identify victims residing in countries in which they have existing bank accounts to make the fleecing easier.
Their exploits are often delivered through a booby-trapped Word documents masquerading as the kind of tailored customer inquiry a business would routinely receive and open.
Here's how the scam works:
For example, one scammer had access to a server with over 2.5GB of HawkEye text logs and screenshots, while another server hosted KeyBase logs and screenshots.These scammers consult these logs on a daily basis to determine which accounts are of interest. They primarily seek out email accounts from companies that deal with purchase transactions. Since the scammer’s primary goal is to divert payments from ongoing transactions into their bank accounts, these victims are the most valuable to them.
Once the scammers identify an interesting victim, they log into the victim’s accounts using the stolen credentials and study the different transactions in which the victims are involved.
The tools, tactics and procedures of the Nigerian hackers were a step up from the 419 scams, but still fall dramatically short of the well-oiled targeted malware campaigns of which El Reg security readers will be all-too-familiar. ®