This article is more than 1 year old
Redmond boffins build coffins for exploit kits
'Kizzle' tool spots and crimps hackers' automation tools
Microsoft boffins have crafted what they say is the world's first platform specifically designed to kill exploit kits.
The tool goes by the name "Kizzle" and is a fast signature compiler that targeted the common practise of code-reuse by malware authors, and could generate identifying signatures weeks ahead of current anti-virus techniques.
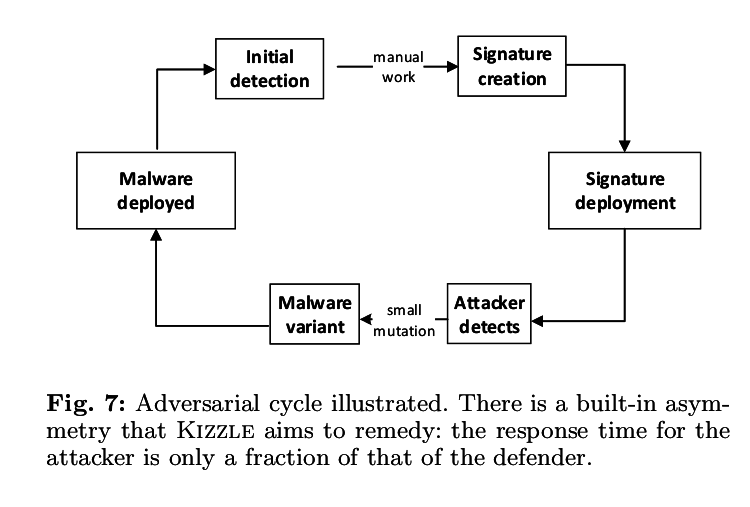
Exploit kits are an effort to package attacks so that bad guys can stop making number plates and instead move to higher-value work in their chosen specialist fields. Ransomware fiends, for example, have most recently moved to this model leaving the process of breaking into systems to the exploit kits.
A trio of Bens, surname Stock, Livshits, and Zorn from the University of Erlangen-Nuremberg and Microsoft say in the paper Kizzle: A Signature Compiler for Exploit Kits (PDF) that the bundles looked wildly different until it unpacked on machines.
Here the similarities in the underlying fingerprinting and exploitation code are revealed to be consistent between versions, a fact that is detected and exploited by Kizzle.
“Our analysis of some of the code found in exploit kits shows that while the actual JavaScript delivered by kits varies greatly, the code observed after it is sufficiently unpacked and de-obfuscated varies much less,” the authors say.
“The approach taken by Kizzle is based in our observation that, while exploit kits change the malware they deliver frequently, kit authors generally reuse much of their code from version to version.
“Ironically, this well-regarded software engineering practice allows us to build a scalable and precise detector that is able to quickly respond to superficial but frequent changes in exploit kits.”
Kizzle produces anti-virus signatures for exploit kits that throw JavaScript at browsers and better and faster than those which human analysts could produce, the team says.
False positives and negatives came in at fewer than than .03 and five percent respectively using cloud bots over a month-long test, a vast improvement to that of commercial anti-virus.
The team uses the example of the popular Nuclear exploit kit which underwent more than a dozen changes between January and August last year, almost all of which were superficial alterations to the packer only.
Others among the most popular exploit kits in active use changed on average only a few percent, even registering less than a percent of difference over a month.
Kizzle will fizzle if exploit kits become polymorphic and change its unpacked forms, a feat that other research indicates is feasible.
The authors say the detection would best occur in the browser, adding that Kizzle fits “seamlessly” into existing anti-virus systems.®
