This article is more than 1 year old
NOT OK GOOGLE: Android images can conceal code
It's been fixed, but hordes won't have applied the upgrade
Someone's found (yet) another nasty security flaw in Android, by crafting a way to pack malicious software to look like images.
The good news is that disclosure was kept back until Google had put a fix in place; the bad news is, of course, the huge number of phone-owners who never update – either through choice, ignorance or that their handset-maker holds back upgrades.
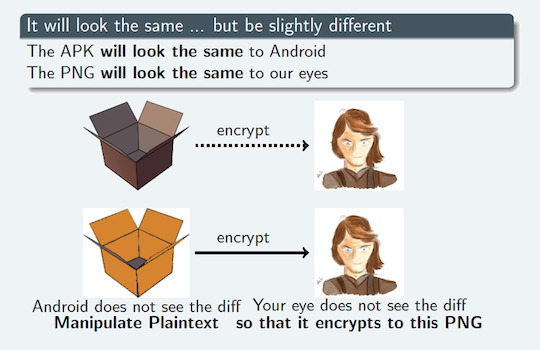
The researchers have found that it's possible to trick the Android app wrapping system so that an image can be wrapped up with malware, and delivered inside an innocuous wrapper app, which gets past both security apps and Google's Bouncer.
The basis of the attack is a custom encryption package (which they dubbed AngeCrypt) that makes the malicious APK look like a valid PNG image file (other image formats work as well).
As the researchers, Axelle Apvrille (Fortinet) and Ange Albertini (Corkami), write in their Black Hat paper from last week, “it is possible to encrypt any input into a chosenJPG or PNG image … the code is able to transform this unsuspicious image into another APK, carrying the malicious payload”.
“Static analysis, such as dis-assembly, of the wrapping APK does not reveal anything particular about that bytecode (apart if weundo the encryption packing)”, the paper continues.
AngeCrypt makes a malicious package look like an innocent image
The AngeCrypt tool, here, works by appending some of the image data after the end of the APK file created by conventional means. That, as they point out in their paper and Black Hat slides, breaks the unpacker at the target, because there's too much data after the End of Central Directory (EOCD) marker, so AngeCrypt adds another EOCD marker to trick the “victim”.
That, plus manipulating AES encryption, yields a package that will pass as an image to Android, but install a malicious app.
Google has pitched out a fix for Android 4.2.2 based on prohibiting appended data after the EOCD, discussed here. ®
